WhiteJar amplifies
your Ethical Hacking skills
A Community of Ethical Hackers brimming with talent
Are you a cybersecurity expert? Would you like to challenge equally skilled colleagues?
Did you just graduate? Are you looking for an opportunity to expand your knowledge in the field?
Would you like to monetize your cybersecurity skills?
The WhiteJar Community is the first Community in Italy to offer crowdsourced Ethical Hacking services by certified European experts. It’s the most challenging, most rewarding workplace you can find.

Operating model
Our Ethical Hacking Manifesto
1
2
3
4
5
6
7
8
9

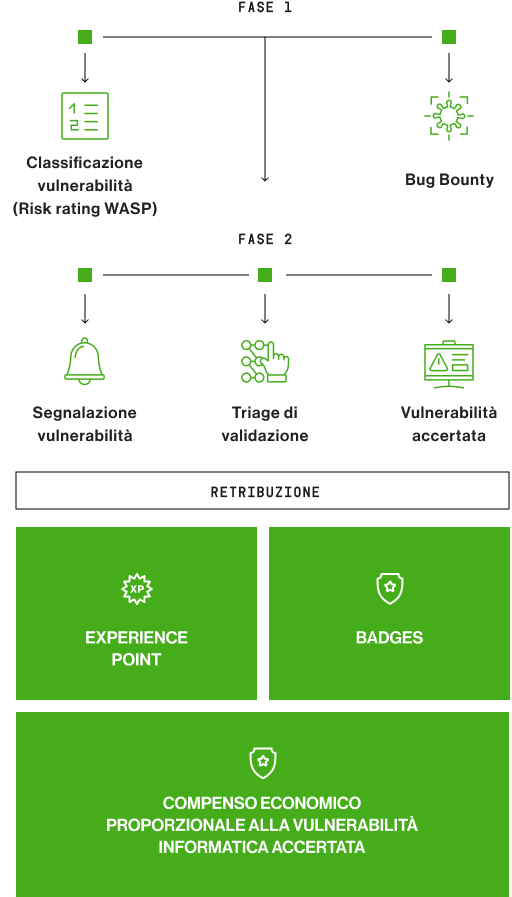
Risk evaluation method and remuneration system
Our payout system is based on OWASP Risk Rating.
The system sorts verified vulnerabilities by risk seriousness based on two factors: probability and impact (technical impact and business impact).
A given vulnerability may be extremely threatening for a corporation but not so much for another.
Once sorted, vulnerabilities get assigned intervention priority.
Every time a vulnerability is verified, the Ethical Hacker who found it receives Badges and Experience Points. A ranking of the best performing Ethical Hackers is visible on the platform.
Remuneration will be set based on the risk represented by the vulnerability found and the financial reward (Bounty) pre-set by the client according to the standards of Bug Bounty tables.
The quality of the work is monitored by the WhiteJar Hacker Teams, according to methodology, technical assets, and strategies implemented by the Hacker.

Program Types

Public and private
Clients can choose whether to have a Bug Bounty program open to the entire Community of Ethical Hackers (public) or target their campaign at a selection of profiled experts (private).
Bug Bounty / Subscription and Rewards / One-shot and Ongoing
During the time covered by their subscription, the Client can launch a limitless number of Campaigns at any time, setting a budget for rewards each time.

FAQ
At this moment we have experience on Private Bug Bounty Programs or Public Bug Bounty Programs. A program can last a precise time period (like 1 month) or stay active forever (until you decide to end it). But our philosophy is that we want to stay flexible and give you the maximum space to engage with the Ethical Hackers community. This means that we can also work on custom programs, as long as we bring value to the community (for example: Capture The Flag program). Being part of the crowd means staying in touch with us, connecting with our teams, and helping us to grow the community. We want to engage with you!
It depends on the kind and criticality of the vulnerability. We can pay from €100 to €10,000, sometimes even more. We will share the payout rules for every program so you can decide if you want to take part or not. However, if the customer involves you in some more engaging activity, we can also pay for extra time or custom projects. We only work on reporting vulnerabilities, not solving them. The report format must be very thorough, and it’s usually made of step-by-step reproducibility, PoC, Suggested Mitigation, Type (e.g. SQLi), Severity (e.g. CRITICAL), and media (e.g. screenshots). The type of vulnerabilities we will accept in every program can vary, and we can define the in-scope and out-of-scope together. For example, we can work on RCE, SQLi, XSS, CSRF, Authentication bypass, Horizontal or Vertical privilege escalation. But, with a particular scope, like for example an IoT device to be tested, we can vary the type of vulnerability and the reward.
No. We are an Ethical community who will ask you to share your ID. We believe that there are excellent Hackers that don’t have a problem sharing their ID and certifications. So, if you only want to appear with a nickname ant stay blind, whitejar.io is not the space for you.
Yes, you can!
All Ethical Hackers must sign confidentiality bonds and are not “unknown” people. We will ask you to subscribe to a code of ethics (Article 2 of our T&C) and follow a certification path (Article 3 of our T&C) which requires, among other things, identity verification, verification of held certifications, and training of various kinds. This process implements logics similar to the stringent verification procedure applied in the EU, called KYC. Accepted certifications evolve during time and can involve: CEH, CISSP, GXPN, OSCP, GWAPT, GMOB.
However, we also accept non-certified Ethical Hackers in the process because we think that the crowd windows and the power of collective consciousness is more powerful than the single Pen Tester work.